by Brian K. Hudson
echo kawnawnaysgee means spider in Cherokee and they both refer to me > readme.txt
“KAW-NAW-NAY-SGEE,” the old woman enunciated carefully, pronouncing each syllable for me as she squeezed my lips open with her strong, bony fingers. This intimate moment was happening in spite of the fact that I had only met this woman a few moments ago. Awkward. Peggy Sixkiller (or Peg, as she said her friends called her—so I should, too), the strange old lady who was now squishing my face as she sounded out the Cherokee word for spider, seemed to be my polar opposite in terms of personality. She was clearly an extrovert; me, not so much. In the few minutes before I became the puppet for Peg’s ventriloquist act, I had introduced myself. Peg had been expecting me. Before long, she asked the question I was waiting for, cocking her head with a mischievous, inquisitive smile.
“So, what’d a sweet, young girl like you do to get in trouble?”
I looked at the ground. “I was arrested for being a hacker,” I mumbled.
“A hacker, huh?” she asked.
“A hacker,” I repeated, this time more clearly. “A computer hacker. I accessed computers without permission,” I clarified.
There were different types of hackers: malicious black hats, goody-goody white hats, and the more complicated gray hat hackers, the kind I was, or, at least, the kind I wanted to be. That’s the reason I had dyed the rest of my hair gray after shaving the sides short. But that was TMI, so I kept my mouth shut.
“So, you snuck into someone’s house and got on their computer machine?”
“Nooooo,” my eyes widened. “Nothing that bad. I just access computers on the Web . . . the Internet.”
“How’d you do that?”
I told Peg how I compiled programs to crawl the net through my modem, looking for hidden files, access points, bugs or glitches, anything worth exploring. I didn’t tell her about the incident at school, which had been my biggest hack to date. The security on the school’s system wasn’t all that great, but I felt the data I had found would have given me some bragging rights on the hacking forums I liked to read, if I were the type to brag.
“So you crawl around the Web looking for bugs?” she asked.
“Yeah. Basically,” I answered.
“Why?” she asked.
“Um. I don’t know . . .” It was a good question. It took me a few moments to come up with an answer. “Curiosity, I guess?”
“Hmmm.” She narrowed her eyes and gave me a slight nod. Apparently she was cool with my explanation. “I’m going to call you Spider because you crawl around the Web looking for bugs.” She gestured, making her right hand crawl like a spider across her upraised left arm to illustrate her point. “Yup, you’re a Spider all right.” She smiled.
It was crazy-accurate because spider was another name for web crawlers, which referred to the type of program I coded. Bots, crawlers, spiders: These were all names for code that scoured the Web for one thing or another. I was considering whether or not to explain to Peg the significance of her word choice when she interrupted my thoughts.
“Jaw-law-gees Hee-woe-nee-sgee?”
I stared. “Huh?”
“You speak Cherokee?”
“I can say hello, but that’s about it.”
“Kaw-naw-nay-sgee. That’s how you say your name, Spider, in Cherokee.” That’s when she reached her bony hand up to move my mouth as she repeated the syllables of my newly given name. In fact, Peg never used my real name. She called me Spider, either in English or Cherokee, for the rest of my sentence. It wasn’t a particularly feminine name, but then again, I wasn’t hella-girly like those Rah Rahs jumping around for the crowd at the basketball games.
Late the next morning, the weather was already climbing toward hot and sticky, just like most summer days in Tahlequah, Oklahoma. I slipped into my beat-up Doc Martens and drove my Jeep up to the trailer on the hill at the outskirts of town. I wondered what type of work Peg would have for me. Cooking, cleaning . . . those were my best guesses. I knocked and was greeted by Peg and a blast of cold air as she opened the front door. She stood there in a yellow housedress smiling at me.
“Oh-see-yo, Kaw-naw-nay-sgee,” she said.
“Hi, Peggy, um, Peg,” I said.
“Kaw-Naw-Nay-Sgee,” she repeated, more slowly this time. “That’s what you are.”
“Kaw-Naw-Nay-Sgee,” I repeated, but my mouth fumbled over the unfamiliar syllables. I hoped that my delivery was good enough to avoid her grabbing my face again.
“Uh-huh,” she nodded, happy enough, I guess, with my pronunciation. “Come on in here to the couch. I have some work for you.”
I sat down on the light brown tweed couch, tucking my skirt underneath me, and tried to be discreet as I looked around Peg’s spotless living room. Across from me, hanging upon the wood-paneled wall, was a framed photograph. I peered at the picture. A woman who looked like Peggy wearing her Sunday best stood next to a younger version of herself. Two children, a boy and a girl, stood before the two women, who each rested a hand atop a child’s shoulder. All were smiling for the camera, but Peg’s smile extended to her eyes and seemed more real, more sincere somehow, as though she had been smiling even before the photographer had asked them to do so. The frame was free of dust, and the glass protecting the photo looked like it had just been polished. No cleaning for me, I guessed.
“You want something to eat, Spider?” Peg called from the kitchen. “I got eggs and wild onions, still warm.”
“No thanks, Peg,” I called back. I guessed I wouldn’t be cooking, either.
“Suit yourself. You’re probably full from eating all them bugs,” Peg said. I could hear her chuckle at her own joke. I smiled to myself.
“How ’bout some coffee?” she asked.
“Sure. Black, please,” I added.
Peg shuffled back into the living room, carrying coffee for both of us. She carefully handed me a chipped white mug steaming with black coffee and set her own upon the table next to her matching tweed recliner. Before I could thank her for the coffee, Peg ducked behind the chair and reappeared with two pairs of concentric wooden hoops, holding them up as if I would understand their significance.
“Cross-stitch,” she said, answering the look on my face which probably had huh written all over it.
“Oh.” It was all I could manage in response. What was cross-stitch?
“Here. I’ll show you,” Peg pulled several large squares of white fabric out from a basket behind her recliner. She unrolled them and stacked the fabric on the coffee table in front of me. They each had a hand-drawn pencil sketch of a barnyard animal on top. Sketched beneath each drawing was what I assumed was the Cherokee word for that animal. But the names of the animals were in actual syllabary, writing I had seen but never really understood. Peg placed one wooden ring on the table and centered the penciled chicken on it. She then pressed the other wooden ring over it, making the cloth taut between them. “You just follow the pencil marks making little Xs with your thread, in and out, in and out. Like this. When you’re moving down the line, come from the bottom like this. That’s a backstitch.” She had started the thread down one of the chicken’s legs.
“Okay,” I said, cautiously taking the hoop from her and continuing the pattern of the chicken with the red thread.
“Jee-Taw-Gaw,” she enunciated.
“Jee-Taw-Gaw,” I blurted to avoid those bony fingers.
Peg picked up the design of the pig and started working on the cross-stitching with me.
“What are these for?” I asked, falling into the rhythm of the task: pushing the needle up through the fabric, making an X, turning over the hoop to make sure it didn’t snag, and finally pulling the thread tight.
“Pillows for the kindergarten students. They use them for nap time,” she said.
“Oh, yeah? That’s cool. Do you make much money selling them at the school?” I asked.
“Money? Nah,” Peg said, waving her needle hand to dismiss my question. “What do I need with money? The trailer’s paid for and I have plenty in savings.”
“Oh. Can some of the kids not afford pillows for school?” I asked.
“Possibly. But that’s not why I make ’em,” Peg answered.
“Then why?” I asked.
“It gives me something to do to pass the time.” She paused for a moment as she completed and then inspected a stitch. “But the main reason I make these pillows is . . . well, curiosity. I guess.”
“Curiosity? I don’t understand.”
“Most Cherokee kids, at least here in Oklahoma, don’t speak their own language. I thought these pillows just might spark their curiosity in learning to speak Cherokee.” She smiled. I smiled back, and we continued cross-stitching in silence.
After a few hours, I was happy to see that we had almost a whole farm full of barnyard animals spread across the living room table.
“We’re making good time, Spider,” she beamed at me. Peg began to sew the pillows together after handing me a blank cross-stitch hoop. “Make whatever you want,” she had instructed me. “Let your imagination go wild.” Half an hour later, after she had finished a few pillows, Peg confessed that she knew how to spell more animal names in Cherokee than she was able to draw.
“I can’t draw, either, sorry,” I said, “but . . . you could print clip art from the Web,” I suggested.
“Clip art?” she asked.
“Yeah. You can print all kinds of pictures, animals, patterns, lots of stuff, and then trace them onto the fabric. But you’d need a computer and printer for that.” I paused. “Maybe the library will give you access to print them?”
“Hmm. Maybe,” Peg agreed. “What you workin’ on over there?”
“Just finishing up,” I answered, holding up my loom for her to see. I had stitched the following sequence of numbers into it with bright green thread:
01010000
01000101
01000111
“What on Earth is that?” Peg asked.
“I made it for you. It’s your name, Peg, in binary code. Computer language. How computers talk to each other,” I explained.
“I love it.” Peg’s eyes lit up. I felt a warm glow in my chest.
“I hope those children get curious to learn Cherokee, Peg,” I said.
“Me too, Spider,” she responded.
The next morning, I found myself waking up earlier than normal, feeling eager to see Peg again. I showed up to her trailer earlier than the mid- to late mornings I had been arriving the last two days. The lyrics “she is on the run” were blaring from my Misfits CD. It didn’t occur to me until I reached the last bend in the rutted road that led to her house that she might still be asleep. I turned my stereo down and was relieved to see the lights burning bright inside her trailer as I pulled into the drive. Peg opened the door, beaming at me as I made my way up the steps. She stood at the door in a light blue nightgown. This time, I took Peg up on her offer of breakfast: scrambled eggs with wild onions and black coffee again. After breakfast, we walked into the living room. I sat on the tweed couch, feeling full from breakfast and ready to start working. The cross-stitch binary code that I had made for Peg was framed and hanging on the wall next to her family photograph. When I turned back to Peg, she was facing me and standing with her hands clasped in front of her.
“I have a surprise for you,” she grinned, and then walked into her bedroom. She returned holding a blank pillow in her right hand, which she rotated like she was Vanna White revealing the final letter of the puzzle to display a striking design on the reverse. The expert stitching depicted a spindly gray spider standing in a white web with the syllables
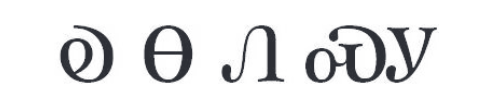
which looked as if they were woven into the web itself. The stitching was much more intricate than the simple technique Peg had taught me for tracing the outlines of the animals on the kindergartners’ pillows.
“Oh. Wow. That’s beautiful, Peg.”
“I want you to have it.” She smiled and handed the pillow to me.
“Aww. I love it!”
Peg stood there smiling and I felt I should hug her, so I awkwardly moved closer. She clasped me, along with the pillow, so tight that I lost my breath for a moment. When I regained access to oxygen, the only thing I could smell was her Youth Dew perfume: spicy and sweet. She held me at arm’s length for a few seconds, peering up at me with a smile. Finally, she let go. “Time to get to work.” She patted my right shoulder and turned to walk toward the front door. She took a ring of keys from a hook near the door and handed them to me. “I got some boxes in the trunk. I need you to bring them in.”
“Sure,” I said. I took the keys and headed outside toward a big blue Chevy Caprice. I thumbed through the keys, finding the round trunk key, and opened it up. I was surprised to find three large boxes that contained all of the components for a personal computer. It was a Compaq Pentium II—not quite top of the line, but Peg still must have spent a grand and a half on it. Four hundred and fifty megahertz of processing speed was probably more than fast enough to do anything that she would want. I snickered to myself, thinking of the unlikely possibility of Peg becoming a hardcore gamer and needing to upgrade to a custom tower with a top-of-the-line Pentium III processor and a graphics card with its own processor for quick pixel rendering. As if, like the Rah Rahs would say.
“Where do you want them?” I asked as I was bringing in the first box with sweat already forming on my brow.
“You can set it up in the kitchen. Thanks,” she replied.
It took longer to lug the boxes into the trailer and unpack them than it did to connect everything to the back of the tower and plug it all into the power strip. When I was finished, I stood back to look at the system. The whole thing took up most of Peg’s small kitchen table. Peg peeked around the corner from the living room, fresh from working on pillows, just in time to see my handiwork. “Oh-sda!” she exclaimed, adding, “That means ‘Good.’”
I repeated the affirmation to her in Cherokee. No bony fingers.
“Welp. Go ahead and power it on.” She motioned toward the screen.
I hesitated. “Um, actually . . . the judge ordered me not to access a computer. So I don’t think I should, like, actually boot it up.” My eyes scrolled to the floor.
“And he also told you to help me with whatever I need, right?” she asked.
“Yeah, but—”
“Tell you what,” she sat down in front of the keyboard, motioning for me to pull a chair up beside her. “What if you just tell me what I need to do and I’ll sit in the driver’s seat?” she asked. “Thataway it won’t be you accessing the computer. It will be me.”
“I guess that would be okay.”
“Good. Now show me them patterns,” she grinned. I walked her through booting up her computer. When the Windows 98 startup sound hummed through the speakers, she looked at me in wide-eyed anticipation. Her lips were pressed tightly together and she hunched her shoulders up in excitement. It had to be the cutest grandma face I had ever seen. I stifled a giggle bubbling up inside me.
“Click here,” I said. Her hand was on the mouse and I placed mine over hers to show her how to click on an icon. She picked up how to double click quicker than expected, and I directed her to the America Online icon because the software was already preloaded. I helped her sign up and she dialed up to the Internet for the first time. She made that same cute excited grandma face again when the screech and the ping-ping of the modem handshake connected us to the rest of the world.
After spending the afternoon printing clip art animals for her cross-stitch patterns, Peg and I stayed up late into the night drinking coffee and exploring the Web. Sites that I had already grown bored with were new and exciting to Peg, and I recited several URLs to her just to see how she would respond to the sites. Peg’s most animated reaction was in response to our visit to the Hamster Dance page. She put her hands to her face and squealed with delight when the animated GIFs of various hamsters and rodents danced around to the looped “Dee da dee da dee da doh.” I had expected her to either love it or hate it (most people felt strongly one way or the other). It was still all I could do to keep from spitting out the gulp of coffee I had just taken when Peg eek!ed at the monitor full of dancing vermin. At 2 a.m., the caffeine finally reached the limits of its powers and I started to crash, nodding off at the table. Peg told me that I’d better just sleep on the couch and that a blanket and pillow were in the hall closet. She didn’t want me to drive home half-delirious from lack of sleep. I asked Peg if she could log off the Internet so that I could call my dad. Even though it was late, I didn’t want him to worry when I wasn’t home in the morning. When I went to the closet to get the blanket and pillow, I heard the ping-ping of the modem handshake again and saw Peg wide awake, her face bathed in the glow from the monitor. I fell asleep wondering if I would be as excited by new technology when I was Peg’s age.
“I want you to teach me how to be a hacker,” Peg said, looking down at me, chipped mug of coffee in one hand and bowl of yellow puffs of cereal in the other. I had just opened my eyes and these were her first words to me of the day, like she had been standing there waiting for me to wake up.
“You . . . what?” Why was an elderly woman wanting me to teach her how to hack? It was too early in the morning for me to understand something this weird.
“I want to be a hacker like you,” Peg repeated.
“Did you even sleep?” I responded, still foggy.
“Nah,” she shrugged at me. “I’ll sleep when I’m dead.” She placed the cereal and coffee on the table in front of me as I sat up and pulled my hair back into a ponytail. Peg sat down on the edge of her recliner. I spooned a couple of bites of Cap’n Crunch into my mouth and tried to process what Peg was asking me. Did she want to be a hacker? Nah, she must not really understand what hacking meant. Did she want to know about the history of hacking? I looked down at my bowl of cereal: Phone phreaking probably wasn’t what Peg had in mind.
“Why do you want to be a hacker, Peg? I mean, what do you want to do?” I asked.
“I’ll show you after breakfast.” She stared in silence at me for a few minutes, then asked me, “What computer did you hack off to get into trouble, if you don’t mind me asking?”
“It’s just ‘hack,’ and I don’t mind,” I answered. Over the rest of my cereal, I explained to Peg how a few of us at the high school had suspicions that one of the coaches who taught geography was favoring his jocks and the most popular cheerleaders. So I hacked into the grade system, printed out everyone’s names and grades for all their classes, and stapled the list to the cork board in the hall. The data showed a sharp uptick in GPA for basketball players in Geography class. I circled those parts to draw attention to the discrepancy. Unsurprisingly, it had caused quite a bit of drama.
“Oh. Is that it?” Peg sounded a little disappointed. “I thought you maybe hacked into the FBI or something.”
“Whoa, nothing like that. The feds would have gotten involved for something that big,” I said. Instead, the tribal court had handled my case and sent me to Peg for community service.
“Then how’d you get caught?” she asked, still literally sitting on the edge of her seat.
“It was stupid, really,” I said. I then went on to tell Peg how a single piece of paper had caused my downfall. I had been so careful. I masked my IP so that it looked like I had accessed the school computer from China and I used rubber gloves to carry the printout just in case they dusted for prints. My printer jammed, however, on the last page, so I just reprinted it. I took the jammed paper—here is the stupid part—and just crammed it into my backpack. So when they searched the belongings of everyone under suspicion (that is, the handful of computer geeks at Sequoyah High School) they found the partially-printed page in my possession. Busted.
“Mmmmm.” Peg contemplated for a moment, then stood up and darted to the kitchen. I followed, carrying my coffee mug. Was she disappointed in me for what I’d done at school? Or maybe she was disappointed that I wasn’t a better hacker. She walked directly to her computer, leaned over to the back of the tower, and unplugged the printer cable. She turned to me and grinned. “No paper trail.”
“No paper trail,” I echoed back to her, and that became our mantra. We said it to remind ourselves to leave no identifying bits of code behind, no fingerprints, no trace of who or where we were.
It turned out that what Peg had in mind wasn’t really hacking. Well, at least not at first. What she wanted to do was to make a version of the Hamster Dance web page that featured characters from the Cherokee syllabary dancing around the screen instead of animals. So I showed her how to download the Microsoft GIF animator and a Cherokee font. I convinced her that we should start small, working with just one syllable at a time. After several tries bent over the long-stemmed microphone, Peg recorded herself pronouncing the first Cherokee character—D—to her satisfaction and saved it as a .WAV file. A little while later, we got the pixels of the syllable to bounce just the way she wanted them to. Then I showed her how to use Notepad to write the few lines of HTML code needed to make a simple webpage. She typed “<title>First Syllable of the Cherokee Language</title>” after the opening <html> tag. After that, all we needed was a little bit of code to display the animated GIF in the center of the page and play the “Aw” sound on a loop in the background. I could tell by the look on Peg’s face that she was pleased.
“Your first web page, Peg. Congrats!” I cheered, causing her to blush. “We should probably add a link to the next syllable, which should be on a separate page. Or we might just do the first six characters of the syllabary. But we’d need to work on the timing of the sounds to make sure they match up with the animations.”
“This might be enough to spark someone’s curiosity, Spider, what do you think?” Peg asked.
“Sure. I’d definitely be curious if I came across this.” Another idea struck me. “Maybe we can add a link to the entire syllabary and a short bio of Sequoyah?”
“How do we put it on the Web?” she asked.
“We could get free hosting with GeoCities or pay for hosting and a domain name,” I said.
Peg interrupted me, shaking her head. “I want to put it up on the Hamster Dance website.”
“Uh . . .” was all I could manage in response. Peg wanting to hijack a popular domain totally caught me by surprise.
“That page has millions of visits. I saw the counter at the bottom of the screen,” she continued.
I struggled for a moment with how to let Peg down gently. “Yeah. That’s not so easy, though. We’d have to figure out the admin password to the site. And even then, it would only be up until they caught the problem and changed the password.”
“Good. Let’s do that.”
And that’s how I started teaching Peg how to hack—well, crack, to be more accurate. Cracking is the art of breaking into a system by guessing the password. Password-cracking programs are a much better approach to doing this than randomly guessing a string of characters. That would take forever. I explained to Peg that cracking software basically tried every possible combination of the available 128 ASCII characters. Because of all the possible combinations, it took a long time to crack a password. We could write that program together, I said, like we did her web page, but I already had a cracking program that I had modified. It was the one I had used to bust into the school’s grading system.
I ignored the voices in my head warning me that this wasn’t a good idea. I showed Peg how to download and install HyperTerminal and directed her to dial into a Linux box that I kept as a mirrored backup of my files at a friend’s house. She downloaded the bash shell script and I showed her how to modify the code. I explained how it ran through a proxy server that masked our real IP address. I also told her that after every few attempts, we would need to change the IP address that it attempted to log in from. The proxy server I used gave the user the option to manually pick from a range of available IP addresses, but I hadn’t figured out how to automate the IP selection in code yet. So Peg would be doing a good deal of clicking.
“All this IP hopping will basically help keep us from getting caught,” I explained. Well, I hoped.
“No paper trail,” she said.
“No paper trail,” I responded.
“Let’s get to cracking,” Peg said with a mischievous smile as she interlocked her fingers and pushed her palms outward, popping several of her knuckles.
I went home early that evening, leaving Peg to her own devices. It was highly improbable that the program would crack the password to the Hamster Dance site overnight. Even if it did crack the site, it would take several months. I figured she’d get bored with clicking after half an hour and go back to a more innocent activity like downloading clip art for her cross-stitching patterns.
When I showed up to her trailer the next morning, Peg answered the door in the same blouse she had worn the night before. Her eyes were bloodshot and she held an empty coffee mug in her hand. Instead of offering me coffee or breakfast, she gave me a quick “hello” and went straight back to the computer. No big deal. I had already grabbed some toast and peanut butter for breakfast at home, and I felt comfortable enough with Peg at this point to rummage through her cabinets for the coffee grounds and filters.
“I’m going to put on another pot,” I told her.
“Yup. Good thinking,” she said without turning from her monitor.
After getting the coffeemaker going, I pulled up a kitchen chair and sat beside Peg. “Did you even sleep last night?” I asked.
“Ahhh,” she waved a hand at me, “I’ll sleep when I’m dead.”
“I’ve heard that one before, Peg. You need some new material,” I teased.
“How ’bout this for new material?” Peg pointed to the screen. I was looking at someone’s email inbox: chet@chetcornmaker.com.
“Who is Chet Cornmaker?” I asked.
“I guess you don’t keep up on Cherokee politics, huh?” she asked.
I shook my head. “I don’t really keep up on any politics.”
“You don’t read the Cherokee Phoenix either, I take it?” She sounded a little disappointed.
“My dad gets it in the mail, but I don’t look at it,” I said, wishing at that moment that I had paid more attention. “So this guy is a politician, a Cherokee politician?” I asked.
“He might become THE Cherokee politician—as in, the Chief—in the runoff election on the 25th,” she explained.
“Oh yeah . . .” I said. I realized a moment later what this all meant. “You mean you hacked into the email of the guy who could be the next chief of the Cherokee Nation of Oklahoma?”
“Yup,” she said.
“But how?” I had helped Peg set the parameters of the cracking program to use FTP protocol in order to gain illicit access to websites. I hadn’t expected her to crack email with it. But the program would crack email faster since personal passwords were far less secure than passwords used for sites administered by professionals. Everyday users usually had stupidly simple passwords.
“The program you gave me had options for cracking email.” Peg scrolled down to a section of the code where several lines started with hashtags. I knew that hashtags meant the programmer was commenting on her code. Her cursor landed on the heading #CRACKING EMAIL. “I just followed the directions there. It told me how to find the company that holds Chet Cornmaker’s website.”
I nodded. I knew she meant “hosts” but didn’t correct her.
“I didn’t understand this other stuff here,” Peg pointed to lines referring to Post Office Protocol and Simple Mail Transfer Protocol. “So I just searched for the company’s telephone number and called them. They were overseas, so it was daytime there. I just asked them for these settings—” she scrolled down and pointed to the information the program needed to crack emails. “I told them that I needed to set email up for my boss on his new computer. I said I had the password but needed the other information, and they were very helpful and gave me everything I needed,” she said with a crooked grin.
“That’s brilliant, Peg!” I said. “That’s called social hacking when you get information like that from a person instead of a computer.”
“Oh, yeah?” she said. “Well, I guess I’m a real hacker now, huh?”
“Yup. You sure are.” I said.
The next morning when I knocked at Peg’s front door, I didn’t get an answer. After a few minutes, I started to worry, so I let myself in to check on her. I opened and closed the front door quietly just in case she was asleep. She needed all the rest she could get with the recent late nights she’d spent staying up on the computer. As I closed the door, though, I could hear her talking on the phone in the kitchen.
“I understand you’re very busy, Margaret. I just thought it would be nice to see you and the children this summer . . . I know it’s a long trip, but you know I can’t travel in my condition . . . Yes, okay . . . but could you at least put ’em on the phone? Oh, swimming lessons? That’s nice—Have ’em call later, then? Oh! Or they could send me electronic mail. I have this new computer—Oh, you have to go? Well, it was nice to chat for a minute. I’ll try to call when you’re not so busy.”
I knew that I shouldn’t have stood there eavesdropping for so long. The conversation was winding down quickly, so I darted back out the door, making as little noise as possible. I waited another few minutes before knocking again. Peg took longer to open the door than usual, and when she did, she didn’t look like her normal, energetic self. She was wearing a dark house dress with a mulberry print. Her shoulders were slumped and her eyes stared listlessly right through me. I was worried that the late nights had taken their toll.
“You feeling okay, Peg?” I asked.
“Oh, nothing serious.” She didn’t look at me. “I think I might just be coming down with one of them summer colds,” she said.
“Need me to get you anything?” I asked.
“No. I’ll be fine. I just need some rest. Tell you what: Why don’t you go home and I’ll call you when I’m feeling better. I might be contagious and I’d hate to get you sick, too,” Peg said.
“Sure, Peg. Get some sleep, okay,” I said.
“Okay, Spider,” she said as I walked back to my Jeep.
I drove home and sat by the phone in my bedroom watching TV. Peg didn’t call that night. Finally, in the late evening, I started cleaning my room because I had nothing else to do. In a pile of neglected papers on my desk, I found a registration receipt for a college prep class I had forgotten that I had signed up for. The class started the day after tomorrow. I worried about telling Peg, that she might think I was trying to ditch her or something.
I tried calling Peg a couple of times the next morning but kept getting a busy signal. Later that day, I was sitting at my desk leafing through a stack of Cherokee Phoenix newspapers that I had borrowed from my dad. I was avoiding studying the test prep materials and I wanted to see a picture of the guy whose email Peg had hacked. It was easy to find pictures of him and the other candidates, as well as several articles on language learning which were actually pretty interesting.
The ringing of the phone startled me. I jumped up from the newspapers and grabbed the phone, dragging the coiled cord with me back over to my desk.
“Hello,” I said.
“Spider?” It was Peg.
“Yeah, it’s me, Peg. You feeling better?” I asked.
“Much. You’ll never believe what I found. Get over here quick!” she said.
“Sure, okay. Be there in a few,” I said, hanging up the phone. I left a note for my dad.
I took a quick shower, changed clothes, and rushed over to Peg’s. She was standing in the open doorway as I walked up to her trailer. Peg looked like her old self again, her energetic smile extending to her eyes. It was hard to believe that she’d been sick just yesterday. She didn’t say a word. She just turned around, swooshing her yellow dress, and I followed her straight to her computer in the kitchen.
“Take a look at that,” Peg said, standing beside the computer and pointing at the monitor.
I sat down in the chair and looked at the screen. It was an email from Chet Cornmaker’s sent mail folder. I skimmed the contents.
“‘Abolish term limits for executive positions.’ What does that mean?” I asked.
“Cornmaker is planning on being Chief for life!” she said.
“Wow. That’s jacked up. Would that even be legal?”
“It’s legal if he gets a law passed saying it is,” Peg answered wryly.
“You know, this reminds me of a Shakespeare play we read in English class. Brutus agreed to kill his friend Caesar because he was afraid that Caesar was gonna become a king and take power away from the people of Rome,” I said.
“I think I agree with Brutus. The Cherokee Nation don’t need a king either,” Peg said.
“So, what do you think we should do?” I asked.
“Well, the runoff election is in a few weeks. Maybe if we can tell enough people what Cornmaker is up to, they won’t vote him in,” Peg said.
“So, like an article in the Phoenix? Wouldn’t we get in trouble for cracking his email?”
“I got a better idea,” Peg gave me her mischievous grin again. “We make a web page about it to replace Cherokee.org.” She slapped her hands together for emphasis.
Hacking the Cherokee Nation’s official website was going to be just as hard as hacking the Hamster Dance page, but I didn’t want to discourage Peg. She was so enthusiastic about the idea. I spent the rest of the evening helping Peg code a simple web page for the task from scratch. I told her how to set up a plain white background and add a large, centered .JPG close-up of Cornmaker we had copied from his website. Above his smiling picture we entered the phrase “CHET CORNMAKER WANTS TO BE KING” in big black font. Below the picture, in equally large font, read: “WE DON’T NEED A KING.” Below that, in a smaller font, we placed a hyperlink with the words, “If elected, Cornmaker plans to abolish term limits for Chief. Click here to read his incriminating email.”
I showed Peg how to use relative path names for the .JPGs (the picture of Cornmaker and the screen print of his email to which our hyperlink pointed) so that she could upload all three files to the same directory. We named the page index.html, which was probably the current landing page for the Cherokee.org website. I helped her modify the cracking program to run a simple script. The script FTP’d the three files to the public_html directory once it was cracked. I wrote down URLs where Peg could find other cracking programs in case she wanted to try them. Cracking admin passwords for sites such as this could take several months, but I figured Peg would at least enjoy attempting it.
It was getting late and I had held off telling Peg about my college prep class long enough. “So . . . I signed up for a college prep class a few months ago. I forgot about it until yesterday. It’s starting tomorrow but it’ll only be for one week. I can cancel if you want me to. It’s no problem,” I said.
“Nah. You need to go so you can get good scores and get into a good college. Besides, you’ll probably like hanging out with people your own age anyway,” Peg said.
“People my age are boring. I’d rather hang out with you. But I already paid for it, so I guess I’ll see you in a week,” I said.
“Knock ’em dead, kiddo,” she smiled and wrapped me up in another one of her oxygen-depriving, perfume-infused hugs before I left.
I spent the next week alternating between studying for the mock college exams and sitting in the computer lab at the high school listening to the teacher lecture about mind-numbingly basic computer skills. I ignored the fact that I wasn’t legally allowed to operate a computer. Everything from the basic computer skills demonstrations to the mock exams themselves was computerized, so I probably wouldn’t get to participate if I followed the terms of the court ruling. And the teacher was from the test prep company, so she probably didn’t even know about the grades hacking incident, anyway. The week was uneventful. The pace of the course was slow enough that I couldn’t help but surf around a bit while the teacher wasn’t looking. I knew that Peg couldn’t have hacked the Cherokee Nation website, but I couldn’t help myself from typing cherokee.org into the browser and hitting refresh every so often just out of curiosity. On Thursday afternoon, the teacher was showing us how to make a simple family budget in Excel spreadsheets. I had already finished and was waiting on everyone else to catch up. I was so bored. The lag was unbearable. I hadn’t checked the Cherokee Nation website that day, so I typed the address into the browser again. I gasped aloud. Instead of the official Cherokee Nation page I had grown accustomed to seeing, there was the page that Peg and I had made, exposing Chet Cornmaker’s plan to abolish term limits.
“Are you okay over there?” the teacher called out. I forgot I wasn’t alone. “Sorry. My bad. I’m fine,” I mumbled. For the last two hours of class, I couldn’t concentrate. All I could think of was rushing over to Peg’s and celebrating with her.
After class finally ended, I sped over to Peg’s trailer, only stopping at the supermarket along the way to pick up a chocolate cake for us to share. It seemed appropriate to celebrate Peg’s newfound hacking abilities with chocolate. When I pulled into the driveway, I saw a car parked next to Peg’s blue Chevy Caprice. I knocked on the door and a strange woman answered. She looked familiar, but I’d never met her before.
“Thanks,” she said, taking the cake out of my hands as if she expected me. She turned toward the kitchen. “Come on in.”
The family photo on the wall reminded me that this was Peg’s daughter.
“Peg must have been very lucky to have a neighbor like you. You must have heard the ambulance last night,” she called from the kitchen.
My heart sank as the words “must have been” echoed in my head. I had a few seconds to compose myself before the woman came back from the kitchen.
“Margaret,” she said, extending her hand.
I shook her hand. “Spider, uh, at least that’s what Peg calls me.”
“She always did love to give people nicknames.” She managed a small smile. “Mom had a million for me until I finally convinced her to use my real name,” Margaret told me. “Would you like something to drink?”
“No, thanks,” I said. I sank into the familiar tweed couch. Margaret sat in Peg’s recliner.
“She really shouldn’t have kept coffee in the house. This wasn’t her first heart attack, you know. The doctor said she had a problem with metabolizing caffeine and it could be genetic. That’s why I never touch the stuff. But Mom did what whatever Mom wanted, regardless.” She shook her head.
“Oh. I didn’t know about the coffee,” I said, my head still swimming.
“Say, you’re young . . . Do you think you could do me a favor?” Margaret asked.
“Sure,” I said.
“I thought since you were younger you might know something about computers. Mom has one in the kitchen,” Margaret said.
“Yeah, I know a little bit,” I said.
“Well, could you reset it? I mean, wipe out the personal information and reset it to how it came out of the box?” She explained, “I’m going to sell it to help pay for the funeral expenses.”
“Yeah, sure,” I said. Margaret went to the bedroom and I collapsed down into the kitchen chair facing the computer monitor. It felt strange to be there without Peg “in the driver’s seat,” as she put it. The computer was already booted up. I pulled up a browser and dialed in to check the Cherokee.org page again. The admin must have caught the hack quickly because the home page was already back to normal. Well, a couple of hours was better than nothing. I searched the computer for the hacking script but didn’t find any code left from her hack of the Cherokee Nation site. I even checked the recycle bin. Good for her, no paper trail. Then I searched for files I wanted to keep, ones that reminded me of Peg. I took her first web page, the one with the Cherokee letter bouncing around, and the one we had built together yesterday, and moved them into a new folder on the desktop. I looked around the hard drive for anything else worth saving, and that’s when I noticed the text file on the desktop named “tospider.txt.” I double clicked the file:
Spider,
I realize that I never told you the Cherokee story about Spider. This is pretty close to what my grandma told me. You’ll probably find different versions, but this is how I remember it.
In the beginning times, it was very cold because no one knew how to start fires. But there was one fire, an old burning sycamore tree, on an island in middle of a big lake. A group of animals decided that they needed to get the fire to help keep everyone warm. Bear went first because he was the biggest and strongest. He swam to the island, but when he tried to carry a hot coal back in his paws, he just burned all his hair black. Snake went next because he was the sneakiest. He swam to the island, but he too couldn’t carry the hot coal. When he tried to put it on his back, the fire burned all his skin black. Spider spoke up and told the other animals that she could bring back the fire, but they all laughed at her, saying that she was too small. Crow went next because he was the fastest. He flew to the island and put a small burning stick on his wing, but it burned all his feathers black before he made it back to land.
Again, Spider told everyone that she could get the fire back to the shore. They still didn’t believe her, but they decided to let her try anyway. Spider had a plan. She said she needed a ride to the island, so Crow told her to jump on his back, and they flew to the island. Spider had learned some technology from watching the dirt daubers build their mud nests. She gathered a little mud and made a small basket just big enough for a tiny ember. Once it had dried, Spider put the ember in the basket and flew back to the shore on Crow’s back. The ember was still glowing and hadn’t burned through the mud basket. All the animals cheered for Spider because she had figured out how to get fire from the island. Since then, because of Spider, we have always had a way to stay warm.
I thought I’d type this story out just in case I forgot to tell it to you next week when you come by.
Keep a fire,
Peg
I read and reread Peg’s note with tears streaming down my cheeks. When I finally wiped my face dry, I moved tospider.txt into the same folder where I’d saved the web pages, dialed into the Linux box at my friend’s house, and transferred them all. Then I rebooted Peg’s computer into command prompt mode.
“No paper trail,” I whispered before typing format C: /s and hitting the enter key. I reinstalled Windows 98 from the CD, shut it down, and boxed up the computer, monitor, and printer. I said goodbye to Margaret and told her that I was sorry for her loss before driving away from Peg’s trailer for the last time.
I still don’t know how Peg managed to crack the Cherokee Nation website. Chet Cornmaker won the runoff election for Chief later that month, but that didn’t really matter. It didn’t take away from Peg’s accomplishment. It had no bearing on what she meant to me. I wish I could have told her about Cherokee being added to Unicode a few months later so that every computer in the world could display the language. I wish I could have shown her my college application, where I’d listed “Cherokee and Binary” under the languages I had studied. But most of all, I wish that I could have seen her smile one more time. Sometimes I dream that I’m with Peg at the moment she finally cracked the password to the Cherokee Nation website. I see her holding her coffee mug and her smile radiates up from her mouth to her eyes, through me and across the whole room. That’s why I upload this readme.txt file to every server I crack, either manually or through one of my bots. I was lucky to know Peg Sixkiller. I want her story to live on through the Web. I think she would have gotten a kick out of knowing her story is out there.
EOF
© 2016 by Brian K. Hudson. Originally published in Lightspeed in June 2016.
About the Author
Brian K. Hudson is a citizen of the Cherokee Nation from Bushyhead, Oklahoma. He has published two short stories in the genre of Indigenous science fiction. His short story “Land Run on Sooner City” can be found in mitewacimowina: Indigenous Science Fiction & Speculative Storytelling. “Digital Medicine” was originally included in the People of Colo(u)r Destroy Science Fiction! special issue of Lightspeed Magazine, which won the 2017 British Fantasy Award for Best Anthology. For more info on that story, see the article on it in the Cherokee Phoenix. Brian currently teaches digital storytelling and Native Studies in Albuquerque, New Mexico. His personal website is http://www.briankhudson.com/.